
As per the research, 2.9 million DDoS attacks were introduced in Q1 of 2021, a 31 percent increase over the same period in 2020. In recent years, organizations have experienced an exponential rise in DDoS attacks incapacitating businesses in no time.
It is impossible to provide 100 percent protection, even for organizations that are well-equipped to deal with these threats. Still, there are a few possibilities that they'll be targeted by DDoS assaults; it's preferable to be prepared to mitigate the damages.
Meaning of DDoS Attack
DDoS or distributed denial of service attacks is one type of DoS (distributed denial of service) attack. This attack incorporates various connected online devices collectively acknowledged as a botnet that targets websites with bogus traffic.
Unidentical to other types of cyberattacks, DDoS attacks do not breach users’ security perimeter. On the other side, they make websites and servers inaccessible to legitimate visitors.
Moreover, DDoS attacks can be deployed as decoys for several malicious operations, including slowing down security appliances and breaching the targeted security perimeter.
The DDoS attacks can be said to be as strong as an extremely visible event affecting the complete base of online users. As a result, it's a popular tool for hacktivists, cyber vandals, extortionists, and anyone else trying to make a point or promote a cause.
DDoS attacks can be one-time or repeated assaults, but the impact on a website or business can remain for days, weeks, or even months as long as the organization works to recover. Thereby, DDoS damages exceedingly any online organization.
DDoS attacks might result in a loss of revenue, destroy consumer trust, force organizations to spend millions on compensation, and harm their long-term reputation.
DDoS Challenges
- DDoS attacks can take a variety of forms, including DNS flooding, overloaded bandwidth, and exploiting cloud resources.
- Hackers are transmitting low-grade "degradation of service" attacks making costly service slowdowns without putting resources completely offline by using methods comparable to DDoS. Sometimes, these attacks pass out undetected by DDoS prevention systems for a longer duration.
- The number of network entryways by which organizations get exploited is growing rapidly as IoT devices proliferate.
- There is a huge demand for end-to-end monitoring technologies to quickly and effectively stop flooding at both the network and application layers.
- DDoS attack victims are targeted multiple times. Hackers don’t stop if an organization is identified as vulnerable.
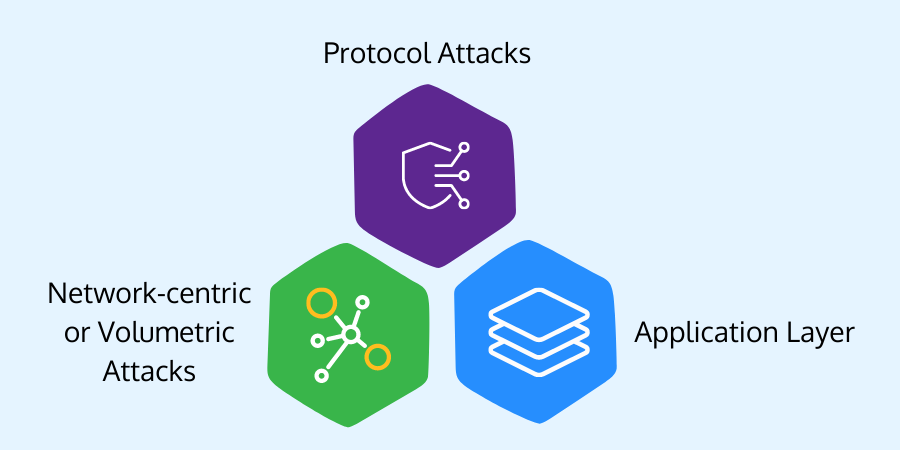
Types of DDoS Attack
There are three types of DDoS attacks;
Network-centric or Volumetric Attacks
These attacks overwhelm a targeted resource by devouring available bandwidth with packet floods. For example, a domain name system amplification attack can send requests to a DNS server by the target's IP address. After that, the server destroys the target with responses.
Protocol Attacks
These attacks use defects in the network layer or transport layer protocols to overwhelm targeted resources. For example, an SYN flood attack delivers a large number of "initial connection request" packets to the target IP addresses with spoofed source IP addresses. Due to the steady influx of requests, the Transmission Control Protocol network takes a long time to complete.
Application Layer
With a significant volume of application calls, the application services or databases get overwhelmed. A denial of service is caused by an influx of packets. A Hypertext Transfer Protocol (HTTP) flood attack, for example, is the equivalent of refreshing several web pages at the same time.
How Does DDoS Work?
In a typical DDoS attack, the assailant takes advantage of a vulnerability in one computer system and turns it into the DDoS master. The assault master system finds additional vulnerable systems. It takes control of them by infecting them with malware or circumventing authentication controls by guessing the default password of a commonly used system or device.
A zombie, or bot, is a computer or network device that is controlled by an intruder. To command the network of bots, often known as a botnet, the attacker creates a command-and-control server. The botmaster is the person who is in charge of a botnet. As it is used to control the spread and activity of other botnet systems, the term has also been applied to the first system recruited into a botnet.
Botnets can be made up of any number of bots, and botnets with tens of thousands or hundreds of thousands of nodes are becoming more common nowadays. There may be no limit to their maximum size. Once the botnet is built, the attacker can flood the target domain with the traffic generated by the hacked devices, knocking it offline.
Because DDoS assaults involve and affect multiple devices, the target of a DDoS attack is not usually the single victim. Irrespective of the main target, the devices which are used to redirect malicious traffic to the target may experience a service degradation.
How to Identify DDoS Attack
DDoS attacks are very difficult to detect. All the attacks simulate a range of traffic caused by legitimate requests from legitimate users across the surface.
However, an individual can discern the fake traffic generated by DDoS attacks from the natural traffic generated by real users in many ways. Here are four signals to identify DDoS attacks;
- Regardless of spoofing or distribution techniques, DDoS attacks can originate from various IP addresses or a single nation or region - may be the place where a user doesn't get much traffic.
- Similarly, a user might get all of the traffic is coming from the same type of client, with the same OS and web browser showing up in its HTTP requests, instead of displaying the distinct networks one could expect from organic visitors.
- All the traffic may strike at a single server, network port, or web page irrespective of being uniformly spread across your site,
- The traffic may arrive in constant timed waves or patterns.
How to Protect Your Device
Here are the possible ways to prevent devices;
- The gateway to a network is the Wi-Fi router. One can change the default password to make it more secure. Considering the fact that security might begin with routers, they can use certain firewall programs built for certain routers, making it simple to administer and secure the network.
- Many IoT devices come with default usernames and passwords. As IoT devices are smart and internet-connected to enhance usefulness and efficiency, the very first thing is to change and update the default credentials.
- Many botnets are controlled by gadgets with no security built-in. So, comprehensive security solutions can help protect important digital devices from known malware variants.






















 Batoi Corporate Office
Batoi Corporate Office