
Introduction
The percentage of cyberattacks is expanding rapidly as more and more illicit techniques are coming into action. Cybercriminals are rookies or elite adversaries who often prefer to use malicious programs to harm a system, individual, or service. According to the Cybersecurity Ventures report, by 2025, different types of cyber crimes will cost 10.5 trillion USD. Over the years, the cost of cybercrime has been growing. One such approach to cybercrime that attackers prefer is by using malware. This article will give you a comprehensive view of malware, its types, how it can harm business productivity, and various measures to prevent such threats.
What is Malware?
Malware is a portmanteau of malicious + software and hence its purpose. Cybercriminals write malicious codes keeping in mind whom to target and which server to infect. Attackers use different channels and mediums to distribute the malware. Some malicious code creates havoc while others work silently. According to Verizon's report, 17 per cent of breaches occur due to malware.
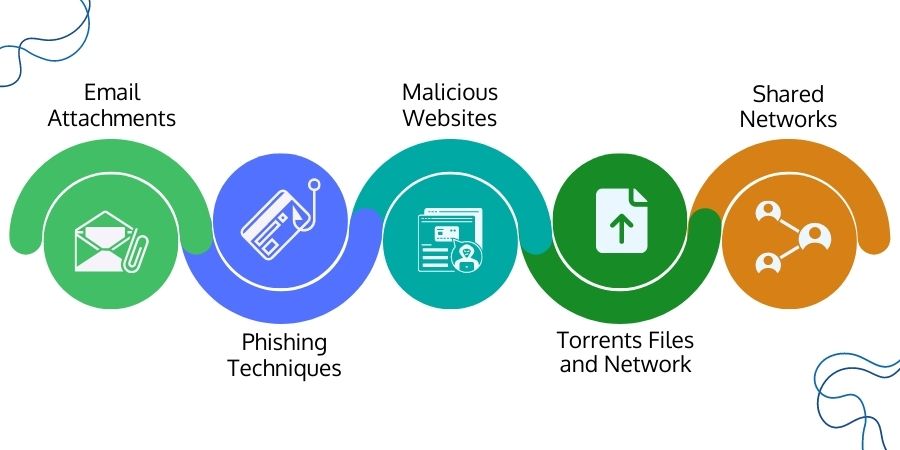
- Email Attachments: Often, large organisations and costly businesses become the target of malware where the attacker uses fake email addresses to send attachments that look legitimate and from a trusted source. These attachments contain malware that gets detonated remotely.
- Phishing Techniques: Attackers often use legitimate counterfeit links and emails. Users click those links or fall into the persuasive words of the emails. These links and emails may lead the victim to download malware.
- Malicious Websites: Many attackers use the drive-by download technique or DNS poisoning attack to lure victims and redirect them to malicious websites from which malware gets automatically downloaded.
- Torrents Files and Network: The file-sharing networks such as "Bit Torrents" are often unsafe. Cybercriminals bind malware into some legitimate files and crack versions of software. When you download those files and software from torrent sites, malware also comes along with those files.
- Shared Networks: A computer infected by malware & remains connected with other systems on the same shared network can also spread malware on the remaining computers.
Types of Malware
All various forms of malware get developed for illicit purposes. Here is a list of the different types of malware that attack enterprise systems and compromise the workforce's systems for unlawful purposes. The type categorisation happened based on their characteristics and working mechanisms.
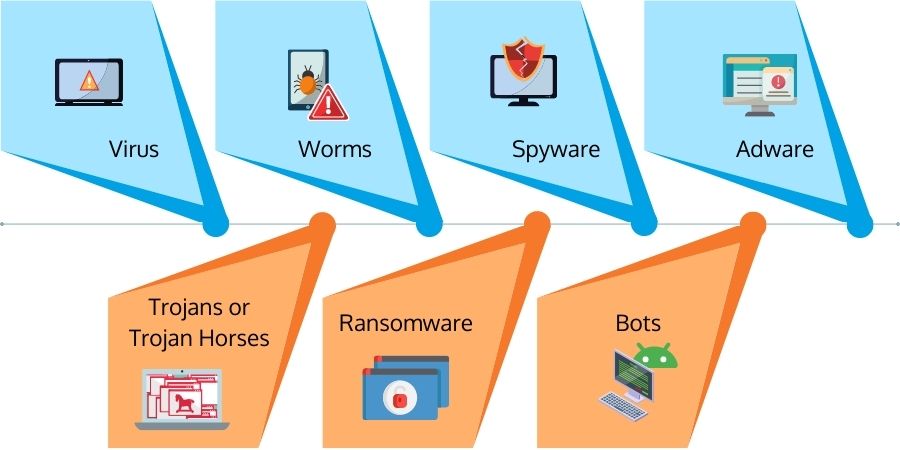
Virus
Computer viruses are malicious programs that spread and replicate with a motive. Their motive is to disrupt the normal working of the system & cause an operational issue, damaging the files or data leakages. There are various sub-categories of viruses. Based on their working mechanism, they harm distinct components of the computer. Usually, computer viruses come attached to an executable host file. When users double-click these infected host files, the virus gets triggered and infects the system. Different types of computer viruses can harm the system. These are:
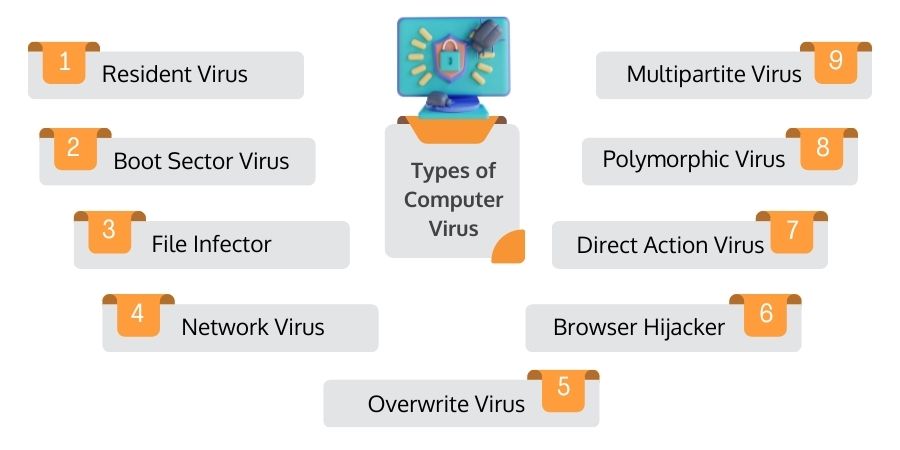
- Resident Virus: These types of viruses get multiplied by infecting applications on a host computer. Usually, these viruses conceal within the computer’s memory and load their replication module to eat up the memory or infect other files.Resident viruses replicate themselves and continue the infection process when an infected app gets opened unknowingly by a user.
- Boot Sector Virus: The booting process occurs every time we switch on the computer. This type of virus targets the booting process & infects the Master Boot Record (MBR). It injects its code into the hard disk's partition table & then crawls straight to the main memory as the operating system gets loaded into the memory. One can effortlessly identify the virus when they see issues in the boot-up process, hard disk partition unable to locate, poor system performance, etc. Today, lots of modern computers come with boot sector safeguards.
- File Infector: These are the most well-known virus type. As the name suggests, mainly targets the files and infects them by overwriting them the moment someone clicks it. Such virus type can quickly spread across systems, external storage devices, and networks & infects mainly the executables such as files with .exe or .com extensions. Any attacker can attach such infected programs with executables. These viruses also come through other infected pen drives or the drive-by-download technique.
- Network Virus: These viruses are too deadly as they can disable or halt your computer network. They disable the essential files the operating system uses to run the internet. These viruses also replicate through triggering and may come through external storage devices like pen drives or other flash drives. These are hard to discover and may come from other infected systems or networks. Various network devices also get infected because of this virus. Therefore, users should only browse or navigate through a trusted network and must deploy antivirus software to stay ahead of such threats.
- Multipartite Virus: This virus uses different techniques and approaches to spread and infect computers. Such viruses remain in the various storage units & spread through diverse drives and file content.
- Polymorphic Virus: "Poly" means multiple, and "morphic" means to change - hence the name. These are complex variants of viruses that create modified versions within themselves to avoid getting detected by antivirus yet maintain the same basic infection routines after every attack/threat. The entire execution of such viruses relies on mutation engines to change their form every time they infect a system.
- Direct Action Virus: They are a class of self-replicating virus that directly infects the main memory. From there, it infects all programs, folders, and files in the autoexec.bat path. It hampers the system's performance and can even destroy all data on the computer's hard disk or externally injected USB device attached to it.
- Browser Hijacker: This virus will straightway attack your browser's settings and implicitly change the settings to lead to malicious sites. Apart from changing to malicious sites, it replaces the homepage, changes the default search engine, deletes the plug-ins or other browser data, and edits the new tab page. Such viruses might also contain adware that can cause unwanted advertisements and malicious pop-ups.
- Overwrite Virus: These are other dangerous variants of the virus that deletes or replaces the file content or code modules with malicious ones. All files from different operating (like Windows, Linux, Chrome OS, and Apple) can become the prey of this virus. Once a file gets infected with overwrite virus, there is no way to retrieve the original file.
Worms
Worms are other malicious programs that can spread, self-replicate, and propagate. They can self-replicate from one system to another without human intervention or interaction/triggering. Worms often look for known exploits & get spread through the network (internet or LAN) or spam emails from one system to another.
Trojans or Trojan Horses
Trojan horses are dangerous malicious code or program that looks legitimate. They covertly work in the background and have the potential to take control of your system. The primary intention of Trojans is to destroy your system's typical workflow, disrupt the operations of various peripheral devices or drivers, steal sensitive data, or perform harmful actions over the internet. They spread through pirated software, email attachments, drive-by downloads, torrent files, apps from non-reputed websites, pen drive data, etc. They act as a bonafide app or file by binding with legitimate files to trick victims, and once they gain access to the system, they can perform malicious actions as written in its code.
Ransomware
Ransomware is another monetary-driven malware that encrypts all the files and folders of the victim's system and asks to pay a ransom against the decryption key. Hackers also keep hold of such data until they get the payment for the amount they demand. In some cases, even the paying of ransom also does not work, and the victim might lose the files and other essential data even after paying the ransom. These are newsworthy malware and often cover news headlines. Such malware mainly targets healthcare systems, railway networks, telecommunications firms, corporate servers, ample cloud storage, and government systems.
Spyware
Spyware is one of the most compelling reasons to steal the victim's digital privacy and personal details. Spyware is an intelligent form of malware that secretly monitors all the activities of the victims and reports them back to its creators. By keeping logs of the keystrokes, this malware can keep track of all the passwords and other activities, like what websites the user visits or how much time the user spends on a particular platform. Some anti-malware and antivirus programs can help detect such spyware. Some spyware comes as a browser extension or a Trojan's feature.
Adware
Adware is malware that serves unwanted or malicious advertising, which can be harmless or might contain irritating or malicious programs hidden within them. These malware-based ads will pop up continuously in between your work, making it difficult to progress in your work smoothly. Furthermore, these ads might also make the victim download harmful malware if the victim clicks it. Ad-remover tools and adware-removing programs can help save your system from such ads.
Bots
These are automated and harmful malware that requires minimum or no creator's intervention to perform their illicit tasks. A bot-infected system can spread the bot to other devices creating the botnet. Cybercriminals can launch massive attacks by using infected zombie computers and commanding them from a single computer. DDoS attacks become possible with the help of these bot malware.
How to Protect Your Systems against Different Forms of Malware?
Modern malware is smart enough to exploit weaknesses in your software, hardware, network infrastructure, architectural design, or programming loopholes. Infected corporate computers will slow down the system and thus slow the employees' work.
Some spyware and Trojan also steal sensitive corporate information & can bring huge losses to the business.
Ransomware attacks are severe and can cost billions of dollars or damage the brand's reputation. These attack vectors can reduce an organisation's corporate productivity and typical workflow.
Whatever the way is, professionals and cybersecurity experts must defend against malware with a multi-prolonged approach. Here are some of the primary measures enterprises and every individual - belonging to an enterprise or their home system must take precautions to protect their systems and networks from malware attacks:
- Every day, security and anti-malware companies identify nearly two million malware threats. Therefore, enterprise systems should install anti-malware and anti-virus software and update them regularly to stay ahead of such threats.
- All major operating system companies roll out patch updates to fix bugs and flaws in the operating systems so that cybercriminals cannot take advantage of those flaws. These security patches contain fixes for newly released attacks and zero-day vulnerabilities that cybercriminals can leverage through malware.
- Often, cybercriminals use lurking emails with malicious links that either redirect the target victim to a malicious page or might allow them to download malware in the background without the user's consent. Attackers can also attach malware directly to the attachments that can instantly infect the victim's system and all other computers connected to the corporate network. Train your corporate employees not to open attachments or emails from unknown senders.
- Continuous monitoring of the network is another way to prevent enterprise systems from any malicious activity or internal threat. Often, attackers can target to jeopardise the network by injecting malware into the network; so that all the computers can come under the attacker's control. Enterprises can create a separate network by leveraging a robust military-grade encrypted Virtual Private Network (VPN).
- Corporate professionals and individuals should rely on official apps and secure or encrypted (HTTPS) network to prevent their actions and data safe from getting into the wrong hands.
- Enterprises should also keep Managed detection and response (MDR) services and tools that can monitor threats continuously & detect threats. Also, such tools & systems help notify the security team to take prompt action against any such malware threat.
- To prevent your corporate systems from notorious malware like ransomware, enterprises should keep a backup of their data separate and isolated so that in case some or any corporate system gets infected by ransomware - the IT team can recover the data from that backup.
- The cyber-world is highly dynamic, and so is the rapidly growing world of cybercriminals and their malware. Thus, apart from all these measures, enterprises and individuals should also remain up-to-date with the latest malware releases and attacks happening & what precautionary measures security researchers suggest for them.
Conclusion
We hope this comprehension has given us a crisp idea of the various malware types and how the malware behaves differently. We have also gathered insight on how or through what sources malware gets spread and finally discussed the various security measures enterprises and individuals should take to prevent malware-based attacks.






















 Batoi Corporate Office
Batoi Corporate Office