As long as businesses become advanced with technology transformations, including cloud migration, they introduce new vulnerabilities if security isn't prioritized. The attack surface has rapidly expanded with the increasing adoption of Internet of Things (IoT) devices, edge computing, and 5G networks, offering hackers more to target.
Every organization is concerned about cyber security and protection, and digital twin technology holds the potential for a more robust online defense.
Consider a virtual model of IT infrastructure where one can identify technical false, create attack scenarios, and protect against catastrophic attacks before the system is exploited. This is a digital twin helping to access loopholes in an organization’s security posture.
As reported by Accenture, 80 percent of security executives are already using digital twin technology in the corporate security programs.
What is Digital Twin?
A digital twin is a virtual representation of an object, operation, service, or system - updated from real-time data. Digital twins aid the decision-making process through simulation, machine learning, and reasoning and can be used for various purposes such as;
- Design testing,
- Introducing and monitoring development cycles, and
- Inspecting how an item or system would perform in certain scenarios
Digital twins have several varieties;
- Component twins are the fundamental building blocks of digital twins.
- Asset twins are when two or more components collaborate to examine their interactions.
- Users can design a whole system using asset twins to spot opportunities to increase performance with system/unit twins.
- Organizations can employ several system twins to construct process twins, which can then be used to establish a whole manufacturing facility to assess the process's overall efficacy.
The technology gathers massive data regarding performance and outcomes. It might keep track of production systems and determine when a product approaches the end phase of its life. As a result, digital twins are highly beneficial during the product research and development process.
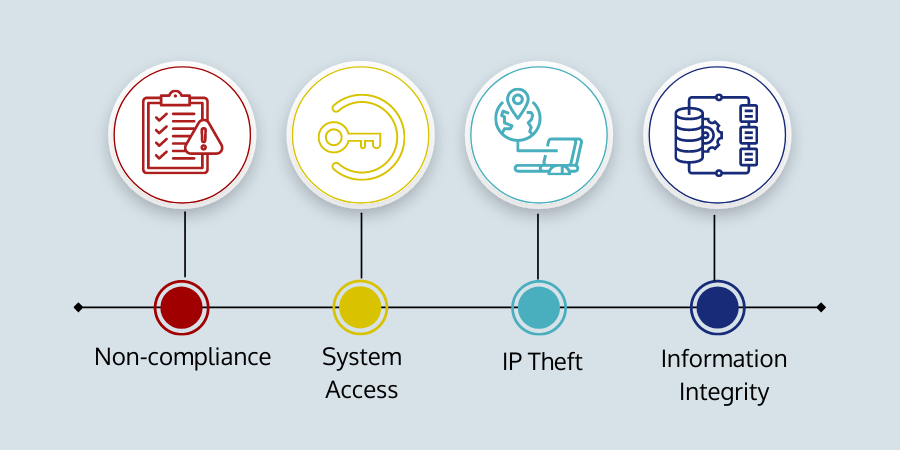
Risk Associated with Digital Twins
There are certain security risks when it comes to digital twins, including;
System Access
If hackers gain access to the digital twin, they can get information from the system or asset it replicates and control these physical assets resulting in uncontrollable behavior.
IP Theft
For instance, the digital twin is a blueprint of intellectual property; hackers could reverse engineer and rebuild that property while conducting research and development on their own.
Non-compliance
Strict privacy requirements, such as GDPR, PCI-DSS, etc., have increased the pressure on businesses to ensure data compliance. If your digital twin is subjected to jeopardy, it may result in significant financial and reputational damage.
Information Integrity
When someone gets access to data and makes unauthorized changes, data can lose its integrity. To protect the integrity of your data, you must acquire the correct data, interpret it accurately, and implement authentication and security procedures to prevent unauthorized changes.
How Secure Digital Twins
Digital twins provide two-way communication between the physical and digital worlds using connected devices, networks, and supporting infrastructure. But, it introduces new challenges for security teams who accept that standard safeguards are incapable of keeping systems and data safe.
There are numerous tools and technologies available to assist in data security and privacy. A user could ensure the safety of digital twin with the following approaches;
Recognizing the Purposes of Risks Assessed
Initially, security requirements will be dictated according to the demands of digital twins. Therefore, it's critical, to begin with, specialized case studies to perceive the information and control end-users' desires. Companies can compute what level of digital twin must be built for assets, processes, or systems and required skills by collaborating with the staff.
For example, digital twin answers are essential for real-time two-way communication, required network's maximum latency, possible threats, data security, privacy concerns, and more. Once users have these answers, it becomes essential to establish a data governance and management approach to secure digital twins, assets, and data.
Structuring Data Profiling Parameters
The next step is to classify and analyze data sources that include legacy systems and new sources such as IoT devices. Companies must decide critical parameters and legal requirements for datasets as part of data profiling practices.
This necessitates answering crucial questions such as
- Is this dataset publicly or privately owned?
- Under what license does it fall?
- Which part of the dataset has to be anonymized?
- If data isn't available, how to produce it?
- How can we transmit data between systems securely? And more.
Proper Data Governance
As the next step, these parameters and standards get integrated with user-specific data governance policies to achieve utmost privacy while minimizing risks. An adequate data management strategy is required to ensure the proper implementation of such policies. For each dataset, companies must ask for identity access management, data reaction, and data residency restrictions to be in place.
Several technologies are helping to implement important data governance activities such as masking, redaction, differential privacy, encryption, and lifecycle management.
Additionally, principles and frameworks can be developed to ensure data is distributed safely, transparently, and with sufficient quality to give meaningful value and insight.
Digital Twins for Cybersecurity
In cybersecurity, digital twins enable new opportunities across the entire value chain. They extend scalability and efficiencies in everything from research, development, testing, and analysis to IP protection and vendor management.
Cybersecurity experts can use digital twins to construct an online, digital replica of every physical asset in a simple form. This digital replica is intended to simulate cyberattacks, exploitation, vulnerabilities, and more to identify possible risks before the original items are attacked.
In certain ways;
- A digital twin can simulate a cyberattack and build decision-making and mitigation strategies in response to the simulated cyberattack. Developers can use a variety of scenarios to test and modify how operators recognize system compromises and respond, keeping the process safe.
- While conventional live attacks and malware with visible symptoms like remote access trojans, crypto locker, and denial of service trojans can be generated in a digital twin, highly sophisticated covert attacks such as Stuxnet, Mirai, Expert, crypto-jacking, etc. cannot be produced.
- A digital twin can replicate various control system compromises in a real-time, responsive environment. By training and testing, operators determine how to use the diagnostic procedure to recognize the extent of compromises, the availability and integrity of the control and safety systems, and how to respond appropriately in case of control loss.
- A digital twin is a pervasive tool for the decision-making process to evaluate the possible threats and suitable responses. This method is similar to how the aerospace industry uses simulators to understand systemic failures required to create, test, and deploy viable troubleshooting and decision-making procedures in real-time virtual environments.
- Companies can use digital twins to track and analyze security flaws and compute the gap between current and planned security standards. It can assist in determining the company's specific security goals and prioritizing cyber risks based on their impact on daily operations.
- With digital twins, users can inspect infrastructure, allowing them to identify and minimize risk exposures. They can anticipate and better handle threats before installing an update if any infrastructure changes are required.
- The digital twin quickly complies with international regulations allowing firms to inventory any resource and calculate quantitative risk exposures before implementing the system.
Collectively, the future of digital twins is endless due to the growing requirements of cognitive capabilities in daily business activities. Therefore, digital twins are acquiring new skills and capabilities, allowing them to continue to generate the insights required to improve products and processes efficiently.

 Batoi Corporate Office
Batoi Corporate Office