
Introduction
With the advent of 4G and 5G technologies, enterprises have become prone to large structured cyber attacks. Enterprises and organizations are facing massive challenges in controlling these different attack vectors. Botnet-based cyber attacks are the most lethal of the various cyber threats that the enterprise faces. Since 2020, botnet attacks are reaching new heights exponentially due to the massive use of the internet and vulnerable devices. If you are new to botnets or want to prevent your enterprise systems from botnet attacks, this article is for you. This article will cater to the different measures organizations can take to secure their enterprise systems and apps from botnet attacks.
What is a Botnet?
A botnet is a cluster of compromised computers and devices connected under one network. Botnet gets formed during the infiltration stage of the cyber attack. The term botnet is a portmanteau of 2 different technical terms robot and network. Attackers who control these bots for making them work as one are called bot-herders. Bot-herder uses special scripts or programs to activate & manage all of them from one central location. These attackers use malware, especially Trojans, to infect other systems and use their collective computing capability to sabotage a server, perform DDoS attacks, send spam, automate login attempts and credential stuffing attacks, etc.
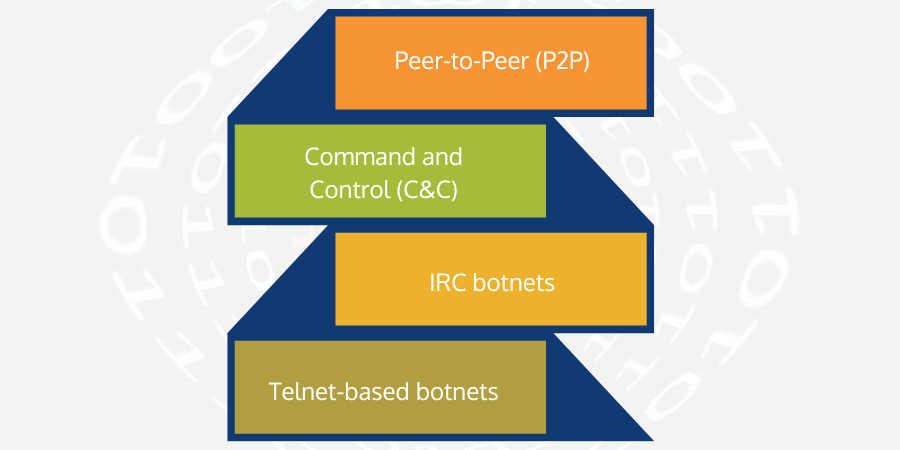
Types of Botnets
We can differentiate botnets based on their communication means, network topology/structure, protocols used, or ways attackers can control these bots. Although there are different ways of managing and controlling botnets, here are some common and trendy ones.
- Peer-to-Peer (P2P): The botnet is categorized based on its network model or structure. The bot-herder controls the botnet in a peer-to-peer (one-to-one) connection rather than controlling from a central location. All infected devices communicated directly to one another as devices communicate in a P2P network architecture.
- Command and Control (C&C): It is the most popular way of controlling and managing botnets. In this botnet network architecture, the attacker uses one computer or system to control all other infected systems (zombie systems) and command those compromised systems (through malware) to attack a target system. Many such malicious campaigns use cloud-based systems to leverage more processing power.
- IRC Botnets: These botnets leverage Internet Relay Chat (IRC) services and focus on low bandwidth or simple transmission systems to control infected systems for large attacks. Such botnet systems are slower but hard to detect as they mask their identity to avoid detection & mimic regular or legitimate internet users.
- Telnet-based Botnets: In this botnet control system, all devices within the network remain connected to the primary command server. The entire structure acts like a sub-category of C&C. The difference is that each infected device or computer can infect another device through malicious scripts that use telnet or SSH ports to connect to each other.
Botnet attacks and ways it damages the system
A botnet attack is a malicious attempt to harm a target system through malicious bots (residing in devices and computer systems). Different cybercriminals with different intentions can launch different attack types through these botnets. These botnets can help attackers launch cyber attacks like buffer overflow attacks, generating fraud traffic, generating auto spamming, automating malicious login attempts, data theft, disrupting the server's standard response system, etc. Some well-known botnets that help attackers perform massive disruption are Mirai, Conficker, Grum, Mariposa, Kraken, Methbot, Ramnit, Cutwail, Necurs, etc.
What is Botnet-as-a-Service?
Botnet-as-a-Service is an online service where elite cybercriminals harvest the bots and their automated scripts. They infect other devices and systems and prepare those bots so that anyone who pays them the service amount uses the botnets residing in the cloud-based platform. In Botnet-as-a-Service, other cybercriminals using it get a dashboard and a secure system to access those malicious services from where they can attempt automated attacks on the target system or server to disrupt its standard service or harm the system.
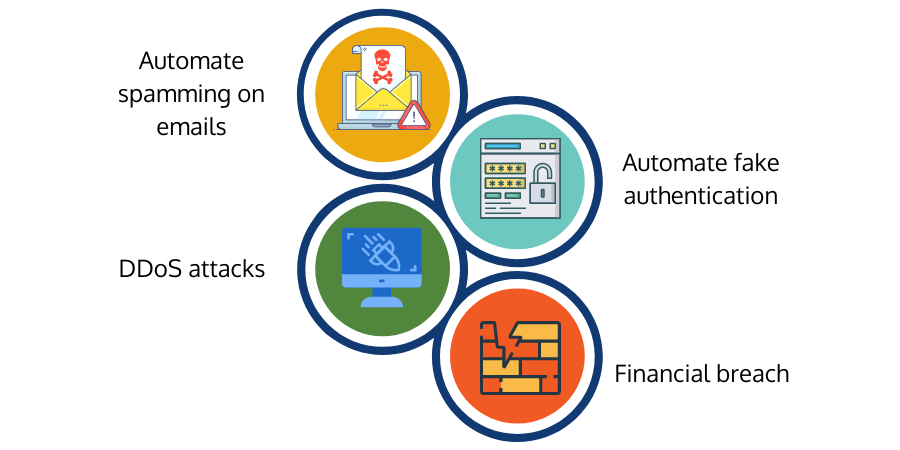
Common goals of a botnet attack
Botnets are hard to detect and often help attackers perform different types of massive and automated attacks. Here are some typical actions that a botnet performs to attack victim servers.
Automate Spamming on Emails: Spams are one of the oldest attack vectors where attackers try to send numerous fraudulent emails to the target victim. Each of these emails contains malicious links, phishing links, malware attachments, etc., that can harm the user or the system. Botnets help shoot multiple spam emails from different systems controlled by one bot-herder or attacker. These automated scripts help send pre-designed templates designed or created by the attacker or social engineer. The Cutwail botnet is an example used to send up to 74 billion messages per day to target systems. These spamming bots also help spread malicious bots to recruit more devices & computers to make them a part of the botnet ecosystem.
Automate Fake Authentication: Attackers design some botnets so that they can automatically attempt malicious logins to different systems and apps. Such botnets use various IP addresses and other credentials to perform automated brute force or dictionary attacks on those enterprise systems to compromise the account and attack the internal system as an insider. Some of these botnets also remain connected to previously harvested and stolen credentials so that the botnet can perform automated credential stuffing attacks.
DDoS Attacks: Distributed Denial of Service is another lethal attack vector that uses a botnet to ping a target server multiple times from thousands of computers and IoT devices simultaneously. DDoS uses compromised computers and vulnerable IoT devices to send unexpected traffic and jam the entire network highway. It sabotages the web app or server's regular traffic or response system.
Financial Breach: Cybercriminals also leverage botnets to compromise financial accounts and steal funds or credit card information. The Zeus botnet was responsible for robbing millions of dollars directly from corporations over a short period. Some other financial botnet does auto mining of cryptocurrencies, while other botnets steal financial details and share them over the darknet to the highest bidder.
How to detect botnet and botnet attacks?
Often botnets are hard to detect as they use specific computing resources. All modern, sophisticated botnets keep updating their behavior to avoid detection by security and defense software. Here are some fundamental attributes that can help you understand whether your system is experiencing a botnet attack.
- When your network or system runs slow or starts acting weird
- Your GPU fan started up suddenly even when your system is not executing any app
- Check the task manager and startup tab to see if your system is over-performing compared to the apps it is currently running
- Unexpected pop-ups and opening of the browser are the signs of Botnet infected system
- A sudden increase in traffic, especially for logical ports (port number 6667 that uses IRC, port number 25, and port number 1080 that the proxy servers leverage)
General Ways of Preventing Botnets for Enterprise Security
There are different stages and mechanisms for preventing botnet attacks at the individual or enterprise level. Here are some prevention techniques:
- Update all antivirus and antimalware software of the enterprise periodically. That can make them detect all the latest malware signatures that can make a system botnet infected.
- Avoid opening unknown emails and attachments from malicious or unknown sources.
- Disable all logical ports of no use in the corporate systems. If you are not a technical person, seek help from a technical or network specialist to perform such actions.
- For enterprise systems, the IT administrator or network admin should monitor all incoming & outgoing traffic closely. It can help detect any anomaly or unusual traffic.
- Leverage multi-factor authentication (MFA) for password-based and passwordless authentication techniques so that botnets cannot automate the authentication attacks, even using credential stuffing.
- Enterprises should enforce adequate entry and exit filtering solutions and practices.
- The network administrator should take care of third-party applications or access requests.
- Also, employees within the enterprises should avoid downloading unnecessary apps from blacklisted sites, file-sharing, and P2P networks.
- Companies can use specialized programs or scripts to monitor failed login attempts to detect automated actions of malicious logins.
- The CISO experts and security heads should not use vulnerable CCTVs and IoT devices within the enterprise premises. Also, they should add additional security codes to the IoT systems to keep them secure from such attacks.
How can developers prevent their servers and apps from botnet attacks?
Apart from generalized techniques of detecting botnet attacks, enterprises that are into robust B2B software development business and cater to large web apps to other companies must take proactive actions during software development to defend against botnet attacks. Here are some precise product development tactics that developers and software engineers can use to prevent botnet attacks.
- Use Google's CAPTCHAs & reCAPTCHA to Prevent Apps: CAPTCHAs are standard security measures that cater to a challenge-response system through which websites and web apps can distinguish robots & humans. We can abbreviate CAPTCHA as Completely Automated Public Turing test to tell Computers and Humans Apart. Such a security mechanism increasingly reduces the number of spamming, DDoS, automated use of online services, and bot-based authentication. Developers can leverage CAPTCHA and reCAPTCHA from popular companies like Google. For this, developers have to generate CAPTCHA/reCAPTCHA API & secret/private key and use it with the HTML code or the application to prevent the web app and its associated server from automated bot attacks.
- Restrict Login Attempts to Eliminate Risks of Account Compromise: Whether it's a mobile app or a web app, they are prone to account takeover attacks. This risky threat allows attackers to steal credentials and take over user accounts making the entire app vulnerable. Often botnet attackers leverage bots to fetch previously compromised credentials and automate the malicious login on apps. To remove such illegitimate automated login attempts, app developers can write separate lines of codes that will restrict the number of login attempts in the app. In most modern apps, the attempts get confined to 5 to 6, and then a notification is sent from the app to the associated email or phone number.
- Use Data Packet Analysis Libraries & Network Filter Modules: Developers can also prepare a separate screen where they allow the app admin to monitor networks and data packets. That is where developers often include traffic dissectors and data parsing libraries & use them to write particular code that can detect suspicious traffic coming into the app. Keeping an eye on the incoming data packets helps prevent the app from malicious packets.
- Load Balancers: Hardware like load balancers can also help secure online applications and infrastructures from multiple botnet attacks like DDoS. They act as a traffic cop and distribute incoming network traffic smartly to a pool of servers so that one server does not get pressurized due to excess network traffic. Modern load balancers also come with smart algorithms that efficiently detect unwanted or unsolicited traffic and discard them from accessing the server.
- Secure and Seal Logical Ports in Apps/Systems: Cyber attackers often design botnets to check/scan all logical ports, and if found open, these bots try to exploit these open ports. The shortcoming of these ports and zero-day vulnerabilities associated with these ports often cause a devastating outcome for the app and its users. Some bots harness these open ports to steal sensitive credentials and information. To prevent such automated port sweeping and data sharing through unencrypted ports, developers can use socket programming to close unused ports that the app leverages. By restricting the app to use encrypted ports like 80, 443 & 21 only through socket APIs and libraries, developers can prevent unencrypted transmission over the network and secure it from botnets that can steal sensitive data from within the app.
- Third-party Dependencies, Packages & Vendor-supplied APIs: Many third-party vendors cater to botnet prevention tools through online API services, packages, or libraries. Developers can buy and implement those premium packages, dependencies & APIs and integrate them into their apps. Enterprises can also leverage many CIAM solutions in their authentication screens of the app to prevent them from botnet attacks. Most modern CIAM solutions come with bot detection and prevention mechanisms. Network Intrusion Detection Systems (NIDS), Network sniffers for detection/prevention, Rootkit detection packages, etc., are some popular tools that can work in close combination to thwart botnet attacks.
- Machine Learning Techniques for Botnet Prevention: Analyzing the behavior of botnets minutely is another mechanism developers can use to mitigate botnet attacks on the app. To prevent apps & servers from attacks like DDoS, automated brute force & credential stuffing, developers can train machine learning models through large datasets (containing data patterns about how botnet attempts automatically) to understand bot behaviors. There are specific bot datasets that can help prepare these ML models. Machine learning engineers can work closely with app developers to develop intelligent modules that can analyze past login details, authentication patterns, automatic IP address switching, malware signatures, and other classifications to identify botnets & shield the app against them.
Conclusion
Botnets are a chain of compromised or infected computers and devices (especially IoT devices) that can sabotage a system, app, or server. Cybercriminals also leverage them for other automated purposes & massive attack attempts like spamming, auto-login attempts, distributed denial of service attacks, financial data stealing, etc. This article has covered the 360-degree view of botnet attacks and how enterprises and corporations can prevent their entire intranet, extranet, network, and infrastructure from this devastating attack. This article finally covered the prevention mechanisms enterprises should take from a general perspective and the developer's end to prevent systems, apps, and servers from different botnet attacks.












 Batoi Corporate Office
Batoi Corporate Office