
Threat hunting is a proactive strategy for internet security where threat hunters search for security hazards hidden within an organization's network and go beyond conventional detection technologies such as SIEM, EDR, and others. In contrast to passive cyber security hunting tactics such as automated threat detection systems, threat hunting actively seeks out previously undetected, unknown, or non-remediated threats evading your organization’s security strategies and network systems.
This article explains why a sound security posture must be vigilant with threat hunting, its essentials, and how it advances your organization’s network security strategy.
What is Threat Hunting?
Threat hunting scans proactively across networks and endpoints to uncover threats that evade security controls. In this process, threat hunters search for indicators of compromise (IoCs) across an organization's IT ecosystem using manual and machine-assisted techniques. It helps security teams to uncover and respond to unknown threats swiftly and effectively before they cause any damage and disruption via hunting for evidence of a breach.
Threat hunting is a time-consuming and resource-intensive methodology that necessitates a thorough awareness of cyber risks and criminal adversaries' tactics, techniques, and procedures (TTP). Without this level of expertise, organizations may risk and leave themselves exposed.
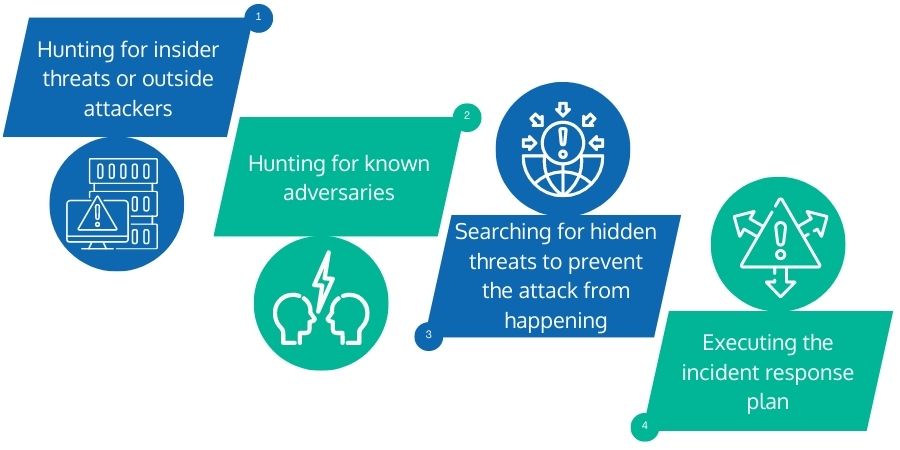
Threat Hunting Activities Include
- Hunting for Insider Threats or Outside Attackers: Identifying threats posed by insiders such as an employee, outsiders, or a criminal organization.
- Hunting for Known Adversaries: A known attacker who is listed in threat intelligence services or whose code pattern/behavior is enlisted on the known harmful applications' denylist.
- Searching for Hidden Threats to Prevent the Attack from Happening: Using persistent monitoring to assess the computing environment and discovering anomalies indicating a threat via behavioral analysis.
- Executing the Incident Response Plan: Discovering a threat and compiling comprehensive information before implementing the incident response plan to neutralize it. This is used to keep the response plan updated and prevent further attacks.
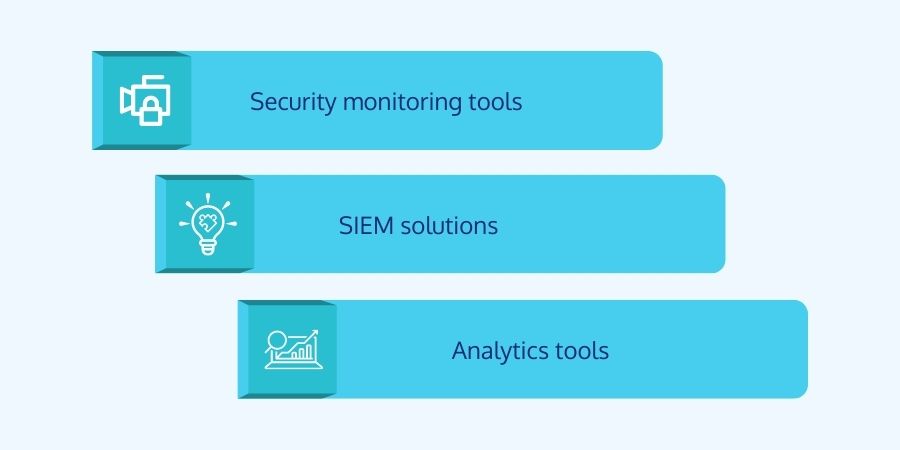
Threat Hunting Tools
To detect suspicious activity, threat hunters employ solutions and technologies. The three major categories are as follows:
- Security Monitoring Tools: Tools such as firewalls, antivirus, and endpoint security solutions collect and monitor network security data.
- SIEM Solutions: Security information and event management (SIEM) solutions aid in managing raw security data and enable real-time security threat analysis.
- Analytics Tools: Statistical and intelligence analysis software generate visual reports via interactive charts and graphs to correlate items and find patterns.
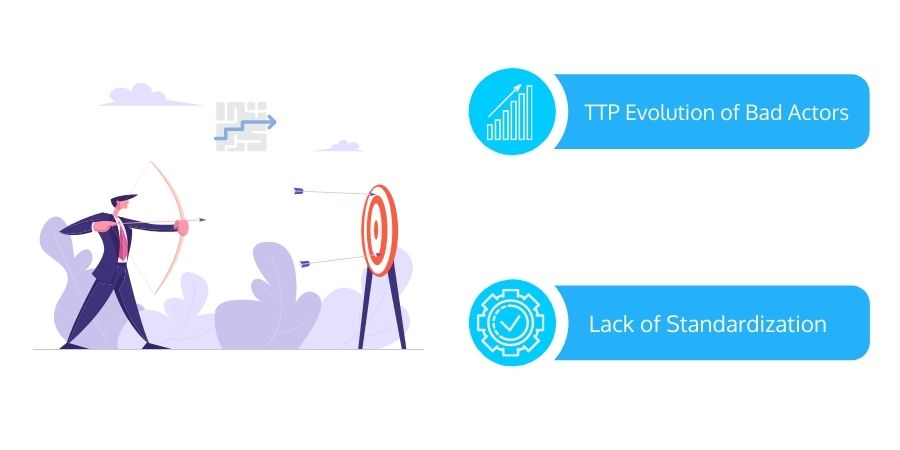
Threat Hunting Challenges
- TTP Evolution of Bad Actors: The challenges for threat hunters will increase with the evolution of bad actors' tactics, techniques, and procedures. The landscape has switched from random malware attacks to more tailored, professional, and targeted attacks. In a field where the adversary moves swiftly, mining data, generating ideas, and conducting investigations all are time-consuming.
The correct datasets in the proper format can make the threat hunter's job more accessible and practical. It’s required to move between metadata, enriched flow records, and packet-level data quickly to reach conclusions. The right combination of automated security tools can thrash the attackers.
- Lack of Standardization: Threat hunters encounter a lack of consistency/standardization and infrastructure constructed around this approach. As threat hunting practices have evolved independently across enterprises, there are common standards and norms accessible for threat hunters because. Unfortunately, articulating more threat hunting standardization may accidentally provide intelligence to malicious actors.
As security threat intelligence and forensics tools advance, threat hunting can augment the balance of power in cybersecurity. Many businesses have implemented effective threat hunting techniques to increase their response times and accuracy, cut dwell (undetected infection) and containment times, decrease the incidence of breaches, and streamline resource allocation. The threat hunters can stay one step ahead by utilizing their expertise and a proactive mode of operation that seeks steadily rather than simply monitors and waits.
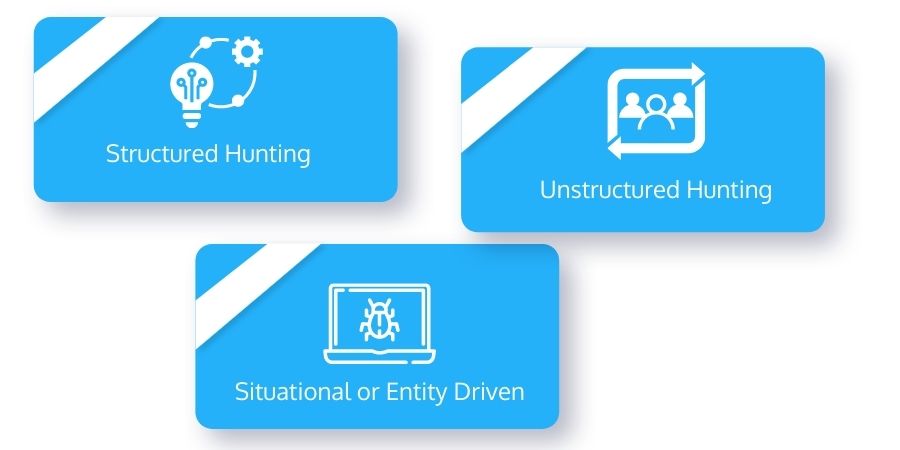
Types of Threat Hunting
Threat hunters start with a hypothesis depending on security data or a trigger. The hypothesis or trigger provides more deep research about potential dangers. These further investigations are classified as follows:
Structured Hunting
A structured hunt is based on an indicator of attack (IoA) and an attacker's tactics, techniques, and procedures (TTP). All hunts are coordinated and based on the threat actors' TTP.
As a result, the hunter can usually detect a threat actor before the attacker does environmental damage. This hunting type employs the MITRE Adversary Tactics Techniques and Common Knowledge (ATT&CK) framework with PRE-ATT&CK and enterprise frameworks.
Unstructured Hunting
An unstructured hunt is launched in response to a trigger, one of the numerous symptoms of compromise (IoC). This trigger frequently prompts a hunter to look for pre-and post-detection patterns. The hunter can research as far back as data retention, and previously linked violations allow.
Situational or Entity Driven
A situational hypothesis is derived from an enterprise's internal risk assessment or a trends and vulnerabilities study associated with its IT environment. Entity-oriented leads are derived from crowd-sourced attack data, which, when analyzed, reveals the most recent TTP of current cyber threats. Then, a threat hunter looks for these particular behaviors across the surroundings.
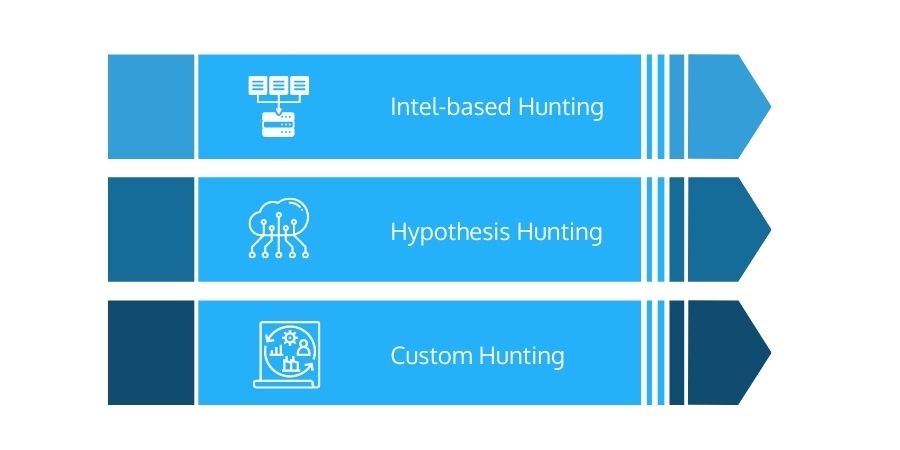
Threat Hunting Models
Intel-based Hunting
Intel-based hunting is a reactive hunting model employing IoCs from threat intelligence sources. After that, the hunt proceeds by predefined rules acclaimed by the SIEM and threat intelligence. IoCs, hash values, IP addresses, domain names, networks, or host artifacts provided by intelligence-sharing platforms can be used in Intel-based hunts. An automatic alert can be exported to these platforms and imported into SIEM. Once the SIEM has generated an alert based on an IoC, the threat hunter can investigate the malicious activities before and after the alert to detect any compromise in the IT infrastructure.
Hypothesis Hunting
Hypothesis hunting is a proactive hunting strategy and uses a threat hunting library. It follows the MITRE ATT&CK methodology and employs global detection playbooks to detect advanced persistent threat groups and malware attacks.
Hypothesis- based on the environment, domain, and attack behaviors used to generate a hypothesis following the MITRE methodology. Hypothesis-based hunts implement attackers' IoAs and TTPs. The hunter identifies threat actors. After identifying behavior, the threat hunter observes activity patterns to spot, recognize, and isolate the threat.
Custom Hunting
Custom hunting depends on situational awareness and industry-based hunting approaches. It detects anomalies in SIEM and EDR tools and is adaptable to customer needs.
Custom or situational hunts are based on customer requirements or proactively undertaken based on conditions such as geopolitical concerns and targeted attacks. These hunting activities can use intel- and hypothesis-based hunting models based on IoA and IoC information.
Conclusion
Threat hunting is a complicated process but is most successful when approached within the context and needs of the organization by recognizing the types of threats targeting the industry or sector. Successful threat hunting involves avoiding biases and bad analytical habits, leveraging the correct methodology, and understanding which tools and techniques are most appropriate in the threat environment, timeframe, and budget.






















 Batoi Corporate Office
Batoi Corporate Office