Introduction
Enterprises often encounter different cyber threats that cost them millions, if not billions. Some of these threats & malware attacks also damage the company's reputation and often lose their customers' trust. One such severe attack vector by which cybercriminals target enterprises is ransomware. Enterprises should remain aware of the ransomware threat, how they work, and the various ways to prevent it. According to the Cyber Security Ventures, by 2031, ransomware will cost around USD 265 billion annually. According to their prediction, there will be a new ransomware attack every 2 seconds. This article will give you a 360-degree view of what ransomware is, its types, and how to thwart enterprise systems from it.
What is Ransomware?
Ransomware is a specially-designed malware that infects one or many target computers by encrypting all data within the system. It prevents the owners from accessing its file/data and asks the owner/organization to pay a ransom in exchange for releasing those data. Predominantly the attacker demands to pay the ransom in cryptocurrencies. The price can range from a few thousand dollars to tens of thousands of dollars - depending on the type & value of files/data the ransomware captured. Such an attack vector often takes advantage of network, system, and software vulnerabilities and loopholes or mistakes humans commit. Such malware can reside in computers, smartphones, wearables, printers, point-of-sale (POS) servers, or other endpoints.
How Does Ransomware Take Access and Start Working?
There is a wide array of mechanisms ransomware can use to access a system. Some well-known vectors are spam emails, USB sticks, drive-by downloads, DNS poisoning, email attachments, clipboard hijacking, etc. In most cases, the emails or messages come as a file or link that masquerades itself as a trusted one. Once a victim downloads the malicious file or opens the link, the ransomware gets into the target system to infect. Some of them take administrative access and lock the entire system so that no one can open it until the victim pays a ransom. Meanwhile, the ransomware starts encrypting all the files within the system. Only when the victim pays the ransom amount - it automatically decrypts all the files using a particular mathematically derived private key.
Who Becomes the Target of Ransomware?
Several factors can trigger an attacker or a cybercriminal group to target an enterprise. Some attackers do it out of passion, while others do it for monetary benefit. Newbie attackers often target universities that have small IT teams dedicated to security. Elite cybercriminals or attacker groups target financial institutions, government organizations, medical facilities, hospitals, and private companies. They do some in-depth research on how much to ask for the ransom. Then they do some information gathering and look for weak spots in the system, apps, or within humans.
Often government officials & healthcare employees need immediate access to their organization's resources. Attackers try to exploit their urgency or penetrate the organizations' security layers by showing a sense of urgency and deploying the ransomware. Attackers also use spam emails, phishing emails, scamming links, or baiting to lure a target victim into downloading or clicking links that lead to ransomware download.
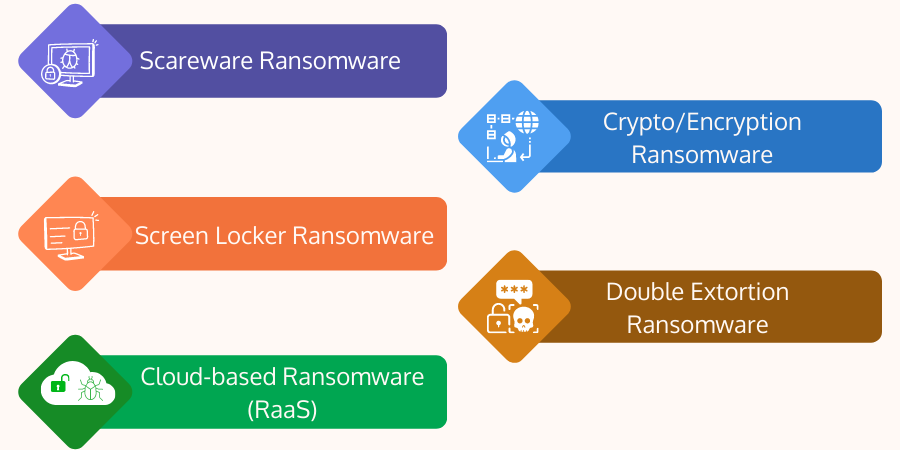
Types of Ransomware
Five different types of ransomware can attack a target system. Security researchers have categorized them based on their functionality & the way they impact a target system. These are:
- Scareware Ransomware: They are not as scary as the name suggests. They are general pop-ups or ads that appear with a message that malware got detected, and you need to pay the ransom to stop its action or stop popping the message. Unless the victim pays the ransom, such pop-ups keep on bombarding and annoying you unless you clear the entire system or reinstall the operating system. These types of pop-up programs often come with illegitimate software or pirated software.
- Screen Locker Ransomware: Screen lockers are ransomware that blocks access to the target system entirely. The target users of such ransomware attacks do not get any chance to access the computer or its files unless they pay the ransom. The attacker uses compromised credentials or social engineering techniques to plant the ransomware into the system. Once the ransomware gets detonated, it locks all possible ways to access the system. Some screen lockers also disable or damage the files through which security experts can gain access, like safe mode in Windows or command-prompt or terminal/based access. Once the ransomware freezes your screen, it will show a section where you have to pay the ransom through cryptocurrency or dollars. Once the victim pays the ransom, the ransomware unlocks the screen & allows the target victim to access the system. Such ransomware does not encrypt any file within the system.
- Crypto/Encryption Ransomware: Crypto ransomware is another ransomware more widespread compared to locker ransomware. It implicitly encrypts all files & drives with robust encryption mechanisms. Then it asks for a ransom in exchange for the decryption key. Some crypto ransomware's latest variants can also encrypt files of the network drives, connected cloud storage, and shared drives. Usually, they spread through suspicious links, malicious emails, illegitimate websites, and downloads. CryptoLocker, Jigsaw, Petya, TeslaCrypt, Bad Rabbit, Locky, etc., are examples of Crypto ransomware.
- Double Extortion Ransomware: Double extortion ransomware is a deadly ransomware type that leverages a specialized technique to exfiltrate a considerable amount of private data from the target system initially. It then delivers it to the creator of this ransomware or the attacker. It is named "doubt extortion" because it extracts private data from the target system(s) & then encrypts all the data and asks for ransom. Here the ransom is not just for decrypting the file. The ransomware threatens to publish or release the private data of the target victim who doesn’t pay the ransom. If the victim fails to pay the ransom, those encrypted data gets destroyed, or the attacker releases all (enterprise) private data to the dark web or sells them to the highest bidder. REvil, Clop, Maze, Conti, etc., are examples of double extortion ransomware.
- Cloud-based Ransomware (RaaS): It is a cloud-based business model where the ransomware creator and operator involve attackers to rent access & use a ransomware strain. The attacker has to pay some amount to the ransomware owner or service provider - which usually ranges from 40 USD to thousand dollars per month. RaaS is for those who lack time or skill to develop ransomware but want to attack a target system for monetary benefit. The complete service works much like a SaaS model. The cost of the service mainly depends on the feature, potential, and complexity of the ransomware the attacker wants to use. In most RaaS models, the attacker has to provide an entry fee to become a part of the service club. Such a service includes 24/7 support and comes bundled with other benefits like forums, user manuals, documentation, user reviews, etc. More sophisticated RaaS operators also allow their subscribers to see the status of the infection by rendering analytics and visuals. Information like total encrypted files, number of private files stolen/copied, and the time required to lock the entire system from all angles, etc. DarkSide, LockBit, etc., are examples of RaaS operators.
Steps Enterprises Can Keep in Mind to Prevent Ransomware Attacks
Various reasons enable attackers to leverage and exploit human tendencies or technical flaws for deploying ransomware. Here are some most well-known factors that enterprises can keep in mind to prevent ransomware attacks.
- Enabling Anti-malware and Antivirus: Anti-malware and antivirus are the preliminary tools to protect against ransomware attacks and variants. Most ransomware comes as malware, so anti-malware and antivirus can identify these threats and isolate them before they get detonated. Next-generation antivirus (NGAV) also has advanced signature and pattern recognition systems to identify zero-day ransomware that is not available in the general malware database.
- Continuous Data Backup: All ransomware has the motive to encrypt most of the files within the target system & asks for a ransom in exchange for the decryption key. Therefore to prevent your data and stay a step ahead of such attacks, enterprises should follow the culture of continuous data backup. Backups of your enterprise data should reside at a different location and system. External hard drives, cloud drives, and isolated servers are some of the best backup examples. Enterprises should ensure that they do not remain connected to the internet or other regular-using computers. A good strategy is to isolate your backup drives and systems because modern ransomware looks for network shares. Cloud servers with multi-factor authentication and high-end security are the best options for backup.
- Patching: Another critical approach to prevent a ransomware attack is to patch the system. Enterprises should patch all the latest exploits available to the target system to reduce the attack surface. Patching covers software, hardware, and network associated with the target system. It can reduce the number of potential vulnerabilities. Most medium and large-scale enterprises allot the vulnerability testing and patching service to recognize known vulnerabilities and resolve them quickly.
- Strong User Authentication: Accessing through Remote Desktop Protocols (RDPs) & using stolen or leaked user credentials are some well-known malicious authentication techniques. Most ransomware attackers prefer these techniques to deploy their ransomware to the target system or server. Thus, robust authentication mechanisms such as passwordless login, multi-factor authentication, and behavioral authentication can prevent organizations from ransomware attacks. Passwordless authentication will make password-guessing attacks invalid. Multi-factor authentication can provide multiple layers of security. Therefore, even if the ransomware attacker knows the password, the second factor, like OTP or email verification, will prevent them from accessing the system.
- Cyber Awareness Education, Corporate Training, and Mock Drills: Ransomware attackers often leverage human errors and try to deploy their malware into the target system. The human errors are mostly downloading attachments from emails, clicking phishing or unknown links, etc. Most modern targeted cyberattacks start through emails and instant messaging services or platforms. To stay ahead of such clever social engineering and attack vectors, enterprises should educate their employees on the different ways, approaches, and thought processes attackers utilize. Then they should get hands-on corporate training on how to react to those scenarios. Lastly, the security team should try simulated drills to check whether employees are falling for the prey.
- Corporate Policy to Use Known Resources Only: Enterprises should set particular security policies. There should have a list of official websites and links from which employees can download or install any file into their system. Even more robust, all the software installations should get a green flag from the IT security team before installation. That will provide a double check and make the security of any enterprise system shielded with better technical protection. Also, the enterprise must install security software like Sophos that can block any black-listed program from installing into the employee's system.
- Network Defenses: Network security is essential for preventing ransomware attacks. Organizations should implement an enterprise-level firewall, web application firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). Security professionals should set up rules and policies for inbound and outbound traffic monitoring. Continuous network monitoring can help organizations identify malicious data packets.
- AMs and Machine Learning-based Security Solutions: Identity and Access Management (IAM) solutions can provide fine-grained privilege management & access control to employees, making them use or access only that particular resource they have permission to access. It reduces the perimeter of the ransomware attack. Also, modern security solutions like IAM come with AI and machine learning capabilities to identify attacks and predict malware attacks through signature or other pattern recognition. Based on behavior analysis, such ML-based security solutions can also detect internal and external threats and notify the security professionals to respond before anything grave happens.
- Implementing Data Loss Prevention Tools: Organizations can practice identifying and preventing data breaches or unwanted destruction of corporate resources and information. Data loss prevention approaches and tools can help extract the data in real-time so that organizations do not face data loss and data leakage. Such DLP tools and techniques pull out all high-priority data before the ransomware takes in and prevent them from leakage.
Conclusion
We hope this article has given a concrete idea of what ransomware is, its types, and how enterprises can prevent ransomware attacks. A cloud backup or any other isolated backup with all or some security measures (mentioned in this article) are some of the best actions to prevent their assets from unwanted ransomware threats. Also, to tackle all modern-day cyber threats, it is essential to leverage artificial intelligence and machine learning algorithms for better prediction and prevention against attacks like double extortion ransomware.






















 Batoi Corporate Office
Batoi Corporate Office