In today’s hostile digital ecosystem, the risks associated with system vulnerabilities are unavoidable, making information exploited, systems corrupted, and brands damaged. Any security compromise in the network, system software, client-side, or server-side level results in massive loss.
To build resilience, organizations require a comprehensive and scalable security infrastructure guaranteeing business continuity, application availability, and high-level protection at every phase of the business's lifecycle.
In these scenarios, security testing emerged as a risk-based approach focusing on software security assurance. This article describes the fundamentals of security testing alongside its principles and types.
Security Testing Tutorial
Security testing is software testing that identifies system vulnerabilities and ensures that the system's data and resources are secure from potential invaders. It assures that the software system and application are free of hazards or risks that could result in a loss.
Security testing of any system is focused on identifying all potential flaws and weaknesses in the system that could result in the loss of information or the organization's reputation.
The objectives of security testing are:
- Identifying threats and vulnerabilities in the system,
- Determining the system's potential weaknesses,
- Detecting all possible security issues in the system, and
- Assisting developers in resolving security issues through coding.
Security testing encompasses the complete range of testing initiatives to guarantee an application's proper and faultless operation in a production environment. It seeks to assess several aspects of security such as integrity, confidentiality, authenticity, vulnerability, and continuity.
Security testing focuses on keeping applications safe and secure by focusing on the many levels of an information system, such as infrastructure, database, network, and access channels.
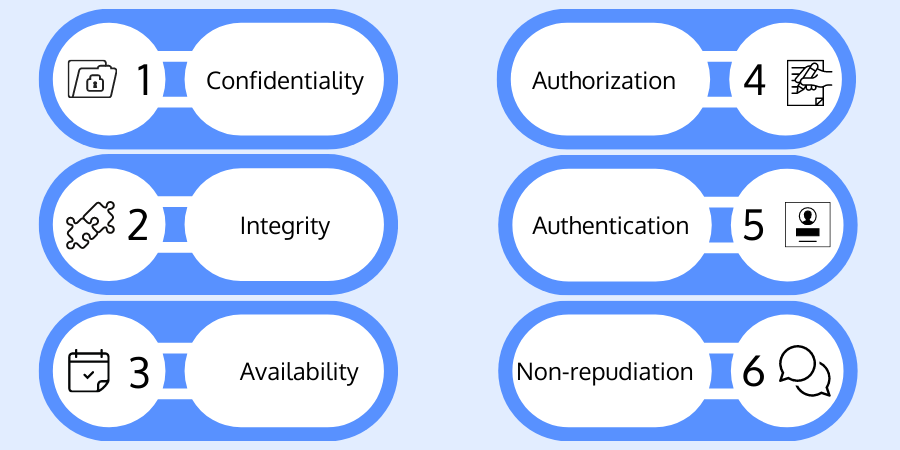
Six Principles of Security Testing
Confidentiality
Confidentiality is the strongest pillar of security testing. It protects stakeholders' interests by avoiding unauthorized exposure of information. Confidential information is details, facts, or figures that are not intended to be shared with third parties.
Integrity
Integrity is the core concept of security testing associated with system and data integrity. The requirement for integrity originates when users wish to confirm that an unauthorized entity hasn’t altered a file or data record.
Availability
The definition of availability implies the capacity to access your data when needed. A data availability plan is imperative in a data breach that can result in downtime, lost productivity, reputational damage, fines, regulatory action, and other issues.
Authentication
Authentication is validating or denying the truth of a feature or attribute of data claimed by an entity. It can be perceived as a series of security methods designed to confirm the identity of an object or person.
Authorization
Authorization is a security method that defines access levels or user/client privileges for system resources such as files, services, computer programs, data, and application features.
Non-repudiation
Non-repudiation is the capacity to prove the identity of a user or process that sent a particular message or did a specific activity. Proof of non-repudiation is an essential element of electronic commerce. It protects businesses from fraud and certifies that a company can count on particular messages or transactions from specific users or computer systems.
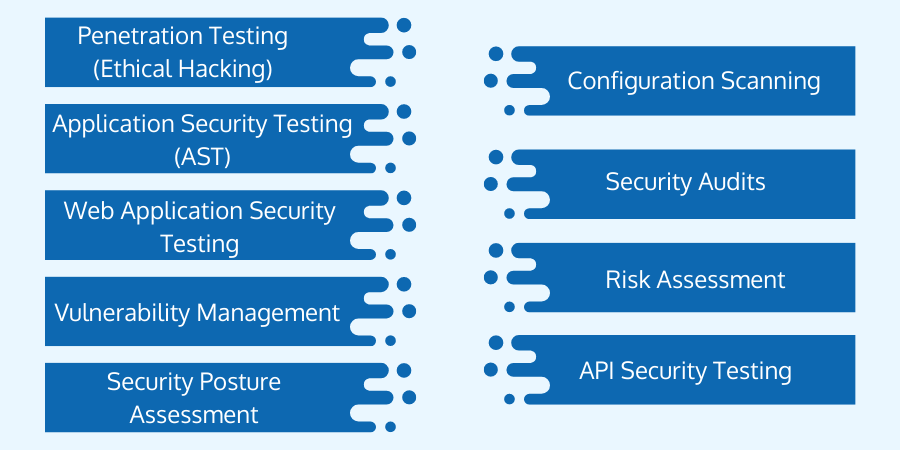
Types of Security Testing
Penetration Testing (Ethical Hacking)
Penetration testing simulates real-world cyber-attacks on an application, platform, operating system, or network in a controlled environment to determine how security measures will behave in a real-world attack. It also detects unknown vulnerabilities such as zero-day attacks and business logic flaws.
Automated penetration testing solutions have assisted enterprises in achieving comparable benefits at low costs and with increased testing frequency. Traditionally, penetration testing was performed manually by a trustworthy and certified security specialist (ethical hacker). The hacker operates within a defined scope, seeking to enter a company's systems in a controlled manner.
Application Security Testing (AST)
Application security testing refers to the approaches businesses employ to identify and eradicate vulnerabilities in software applications. During SDLC, these methods involve testing, analyzing, and reporting on a software application's security posture.
It aims to prevent software vulnerabilities if we fail to discover and remedy them before they are launched in the market. Successful AST results in more robust, safe source code, improved visibility into application security vulnerabilities, and enhanced protection against internal and external attacks.
Web Application Security Testing
Online application penetration testing seeks to collect information about a web application, identify system vulnerabilities or faults, investigate the success of exploiting these flaws or vulnerabilities, and assess the threat to web application vulnerabilities. Web application security testing evaluates whether or not an online application is attackable. It includes both automatic and manual procedures.
API Security Testing
API security testing assists developers in identifying and remediating vulnerabilities in application programming interfaces (APIs) and online services. APIs grant access to sensitive data where attackers exploit them to access internal systems. APIs can be protected from unauthorized access and exploitation by regular testing.
APIs are particularly vulnerable to threats such as
- Man-in-the-middle (MiTM) attacks, in which attackers monitor API communications and steal data or credentials,
- API injections, in which attackers inject malicious code into internal systems, and
- Denial of service (DoS), in which attackers flood APIs with fake traffic to deny service to legitimate users.
To mitigate these risks, an API must have a robust authentication of user requests, user authorization based on the principle of least privilege, and user input hygiene to avoid code injection and manipulation.
Vulnerability Management
Vulnerability management allows a company to identify, assess, report, manage, and fix security flaws across endpoints, workloads, and networks. The security team uses vulnerability scanning technologies to find vulnerabilities and perform manual or automated methods to correct them. A strong vulnerability management program integrates threat intelligence and IT operations knowledge to identify the actual business effect of vulnerabilities, prioritize risks, and address high-priority vulnerabilities.
Configuration Scanning
Security scanning, also known as configuration scanning, is the process of discovering misconfiguration inside the software, network, and other computing systems. It compares systems to a set of best practices established by research organizations or compliance standards. Automated configuration scanning programs detect misconfigurations and generate a detailed report on each misconfiguration with recommendations on rectifying them.Security Audits
Security audits are organized methods for reviewing/auditing an application or software against a predefined standard. Audits often consist of reviewing code or architectures for security requirements, investigating security holes, and evaluating the security posture of hardware configurations, operating systems, and organizational practices. It also assesses adherence to legislation and compliance standards.Risk Assessment
Risk assessment enables organizations to identify, analyze, and classify security threats. It can assist in determining the most significant dangers to an organization's infrastructure and prioritizing system remediation. It can also aid with long-term security planning and budgeting.
Security Posture Assessment
A security posture assessment combines security scanning, ethical hacking, and risk assessment to uncover a business's vulnerabilities and the effectiveness of its current security policies. Detecting gaps in the present security posture recommends modifications and upgrades to increase the security of protected assets.How Does Security Testing Benefit Organizations?
A security breach leads to a loss of customer confidence and revenue. Security threats have expanded dramatically in quality and damage potential. Security testing can assist organizations in identifying vulnerabilities and rectifying security vulnerabilities.
Organizations are conducting security audits and testing techniques to guarantee that their mission-critical applications are protected from breaches or unintentional intrusion. The more comprehensive organization's security testing procedures are, the higher its chances of success in threatening the technology landscape.
Security testing allows organizations to reduce pitfalls arising from the unintended disclosure of sensitive data, lowers compliance costs by simplifying and automating data audit methods, and allows organizations to protect data integrity by prohibiting unwanted access and change.
Adopting robust security testing policies and methodologies ensures that organizations are adequately aligned to global legal and compliance standards.






















 Batoi Corporate Office
Batoi Corporate Office