
The Domain Name System (DNS) is the foundation of the internet, converting user-friendly name-based resource records into corresponding IP addresses. DNS is used to enable authentication and improve the security of internet applications. It must function correctly. Otherwise, internet communication collapses.
A secure DNS is critical for an organization's internet appearance and internal private network applications. Breaches in DNS security are growing more sophisticated and may affect the trustworthiness of the internet. Therefore, the security of DNS is paramount to protecting revenue, users, and brand reputation.
This article overviews DNS security, its types, and common DNS attacks.
What is DNS Security?
When people want to visit any website, they use domain names to specify the website. Computers implement IP addresses to identify several internet-connected systems and to route traffic via the Internet. Here, the Domain Name System (DNS) is the mechanism or protocol that allows domain names to be used on the Internet.
DNS is a key component of the Internet designed as a system for converting alphabetical names into IP addresses, allowing users to visit websites and send e-mails. DNS is structured as a tree-like architecture:
- The first level contains top-level domains such as .com and .org,
- Second-level nodes general, traditional domain names, and
- Leaf nodes are hosts.
Enterprises broadly trust DNS; they use domain names to specify the website or to travel unrestrictedly across network firewalls. However, cybercriminals frequently attack and exploit it.
DNS security is an important component of network security. If enterprises’ DNS infrastructure is compromised, they lose money, witness severe downtime, customer dissatisfaction, privacy loss, and face legal challenges.
A successful DNS security strategy includes a number of overlapping defenses, such as deploying redundant DNS servers, implementing security protocols such as DNSSEC, and mandating extensive DNS logging.
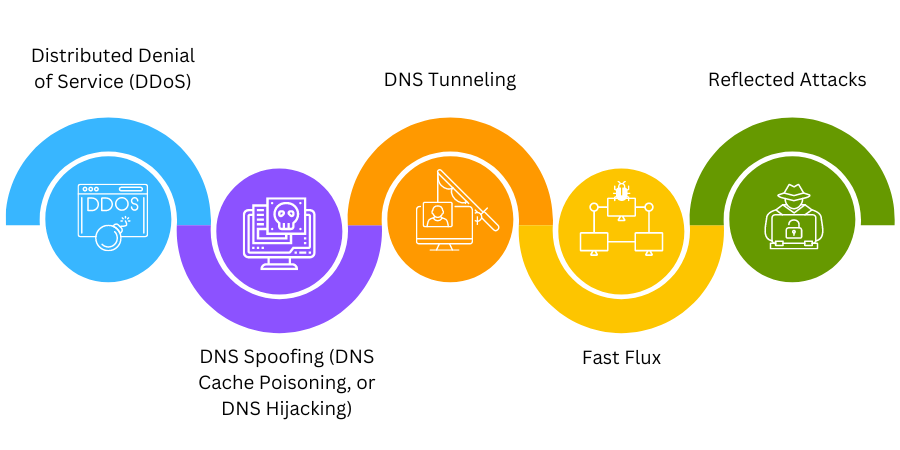
Common DNS Attacks
In DNS attacks, hackers usually target the servers hosting the domain names. In many cases, these attackers attempt to identify and exploit weaknesses within the system itself. Following are some types of DNS attacks:
Distributed Denial of Service (DDoS)
The attacker controls many computers to spread malware and overload the victim's computer with unnecessary traffic. The systems will get overloaded and crash as they cannot harness the power required to conduct the demanding processing.
DNS Spoofing (DNS Cache Poisoning, or DNS Hijacking)
Attackers will reroute traffic away from legitimate DNS servers and to a "pirate" server that are unknown to the users. It can cause the corruption or theft of a user's personal data.
DNS Tunneling
Cybercriminals use DNS for data exfiltration with malware whose DNS requests contain the data being exfiltrated. As the target website’s owner controls the target DNS server, the attackers ensure that the data reaches the server and gets processed, and a response is delivered as the DNS response packet. DNS is a trustworthy protocol; enterprises authorize DNS unrestricted access to pass their networks.
Fast Flux
Attackers usually spoof their IP addresses while performing an attack. Fast flux is a constantly changing location-based data technique to conceal the attack’s source. It hides the attacker's true location and provides them enough time to exploit. Flux can be single, double, or of any other variant. While a single flux alters the web server's address, double flux can alter the web server's address and the names of DNS servers.
Reflected Attacks
Attackers send many requests or queries while spoofing their IP address and use the victim's source address. When these questions are answered, they will be redirected to the victim for attempting attacks.
DNS Functioning: Authoritative Vs. Recursive DNS Servers
Where the authoritative nameserver keeps information on the DNS records, a recursive server positions itself between the authoritative server and the end-user. To reach the nameserver, the recursive server penetrates the DNS tree to access the domain’s records. Both servers hold some key differences:
Authoritative DNS Server
Think of the IP address as the phone number and the person's name as the URL of the website. The phone book connecting IP addresses to their respective domain names is available on an authoritative DNS server. They respond to queries sent by recursive DNS nameservers that give directions to find websites. These responses have the IP addresses of domains involved in the query.
Any region covered by an authoritative DNS server performs two crucial tasks. The server maintains lists of domain names and the associated IP addresses. Next, the server answers queries regarding the IP address corresponding with a domain name.
The recursive DNS server transmits the information back to the computer after receiving the response. Then, the computer uses that information to connect with the IP address and allows users to view the website.
Recursive DNS Server
The recursive DNS server receives a URL that a user types into a web browser. The server examines its cache memory to check whether the IP address is saved. DNS server will send the IP address to the browser if the IP address is already available.
The process of getting the IP will continue for users if the recursive DNS server doesn’t locate the IP address when it searches its memory. The IP address is kept in a recursive DNS server for a predetermined time defined by the domain owner using a parameter known as a time to live (TTL).
Some Measures Against DNS Attacks
- To protect sensitive data, use digital signatures and certificates to authenticate sessions.
- Regularly update and use the most recent versions of open-source software to resolve DNS queries.
- Install suitable patches regularly while fixing bugs.
- Replicate data across some servers so that if data is corrupted or lost, it can be recovered from the others. This could also help to avoid single-point failure.
- To prevent spoofing, block repeated queries.
- Limit the number of potential queries.






















 Batoi Corporate Office
Batoi Corporate Office