
For email security, DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a crucial standard for protecting domains from email spoofing and phishing attacks. Implementing DMARC correctly safeguards our brand's reputation and enhances overall email deliverability. This article delves into the fundamentals of DMARC, its importance, and a step-by-step guide to its practical implementation.
What is DMARC?
DMARC is an email authentication protocol designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. It builds on two existing mechanisms: SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
- SPF: This protocol allows domain owners to specify which mail servers are permitted to send email on behalf of their domain.
- DKIM: This protocol allows the receiver to check that the domain's owner indeed authorized an email claimed to have come from a specific domain.
DMARC adds an additional layer by linking the results of SPF and DKIM to domain alignment and providing a reporting mechanism that allows domain owners to understand who is sending emails on their behalf.
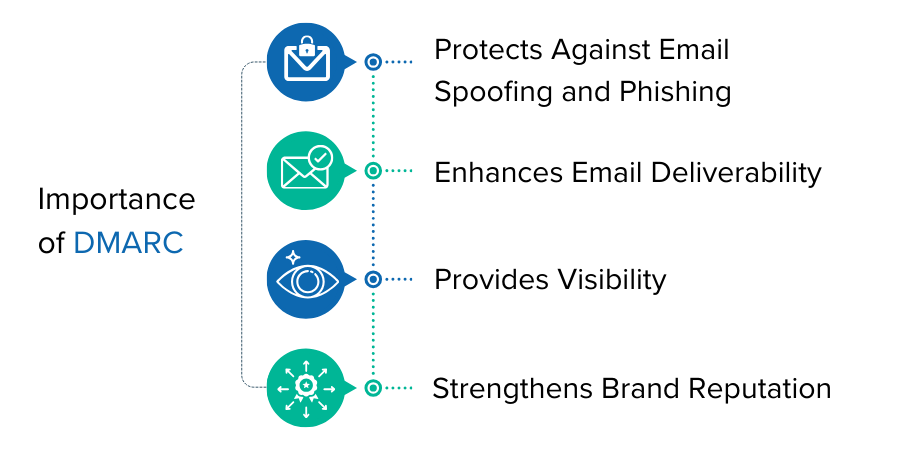
Why is DMARC Important?
- Protects Against Email Spoofing and Phishing: DMARC helps prevent attackers from using our domain to send fraudulent emails.
- Enhances Email Deliverability: By authenticating our emails, DMARC improves the likelihood that our legitimate emails will reach the inbox.
- Provides Visibility: DMARC reports give insight into our email ecosystem, helping us monitor email flow and detect anomalies.
- Strengthens Brand Reputation: Protecting our domain from misuse helps maintain trust in our brand.
How DMARC Works
DMARC works by aligning the results of SPF and DKIM checks with an email's "From" domain. If both checks pass, the email is considered authentic. DMARC policies can be set to one of three modes:
- None: No action is taken; reports are sent to the domain owner.
- Quarantine: Suspicious emails are marked and may be sent to spam.
- Reject: Emails that fail DMARC checks are not delivered.
Practical Implementation of DMARC
Please find the step-wise implementation of DMARC below:
Step 1: Set Up SPF and DKIM
Before implementing DMARC, we should ensure our SPF and DKIM records are correctly set up.
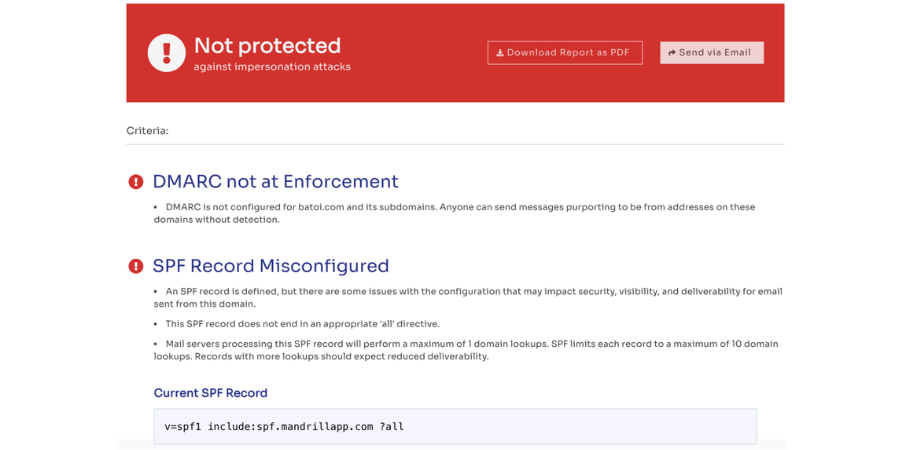
SPF: We create an SPF record in our DNS settings. This record specifies which servers can send emails on our domain's behalf. An example SPF record is:
v=spf1 include:_spf.google.com ~all
DKIM: We generate a DKIM key pair (public and private) and then publish the public key in our DNS settings as a TXT record. Later, we configure our email server to sign outgoing emails with the private key.
Step 2: Create a DMARC Record
We must formulate the DMARC Policy. We decide on the DMARC policy mode (none, quarantine, reject) and then specify the email addresses to which aggregate (RUA) and forensic (RUF) reports will be received. Next, we publish the DMARC Record as below:
We add a TXT record to our DNS settings for the domain we want to protect. An example of a DMARC record is:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-forensic@yourdomain.com; fo=1
Please note the parameters in the record mentioned above:
v: DMARC version.
p: Policy mode (none, quarantine, reject).
rua: Aggregate reports URI.
ruf: Forensic reports URI.
fo: Forensic options.
Step 3: Monitor and Analyze Reports
DMARC aggregate reports provide data on how our emails are being processed by receiving servers. Forensic reports provide detailed information about specific emails that failed DMARC checks. We interpret the reports using DMARC analyzer tools (e.g., DMARCian, Valimail), identify any unauthorized email sources, and take corrective action.
Step 4: Gradually Enforce the DMARC Policy
Initially, we set the DMARC policy to none to monitor email flows without affecting delivery. Once confident in our email ecosystem, we gradually transition to quarantine and then reject to enforce stricter policies.
Step 5: Maintain and Update Records
We must continuously monitor DMARC reports to detect new unauthorized email sources. The SPF, DKIM, and DMARC records should be adjusted as needed. Moreover, as our email practices evolve, we must update our DMARC policies to reflect changes.
Conclusion
Implementing DMARC is critical in securing our domain against email spoofing and phishing attacks. Following the practical steps outlined above, we can establish a robust email authentication framework that enhances deliverability, provides valuable insights, and protects our brand's reputation. Regular monitoring and updates ensure our email security remains effective despite evolving threats.






















 Batoi Corporate Office
Batoi Corporate Office