Privacy and security on the internet have indeed become the topic of interest in recent years. Concerns about data privacy are growing while the companies are constantly trying to reassure users that their data is secure. On the other hand, the governments everywhere are working on some sort of regulation, a consistent law, on big tech companies surrounding data privacy.
End-to-End encryption is one of the tools that companies use to ensure that online conversations remain private. It has become even more critical for users to protect their privacy amidst the ever-increasing use of communication services like WhatsApp, Messenger, Zoom, etc. In this article, we will learn what lies behind the veil of this simple yet effective solution and try to find out if it’s feasible for the government to put some overseer in between the “ends” without risking the user's privacy?
But first, what is encryption?
Encryption is a way to convert a piece of information that might be an email message, a file (such as a PDF, spreadsheet, or document), full-motion video into an obscure format so that it cannot be understood by anyone except the person who has the authority can “unlock” it to the original form.
End-to-end encryption (E2EE) is a communication system where only the communicating users can read the messages. It uses a type of encryption called Asymmetric Encryption that involves two keys – one to encrypt the data and the other to decrypt it. The thing to note is that both the keys involved here are of the receiver. The sender encrypts the data using the receiver’s public key, and the receiver can then decrypt it using his private key. So, we can say that data encrypted by a public key can only be decrypted by a corresponding mathematically related private key.
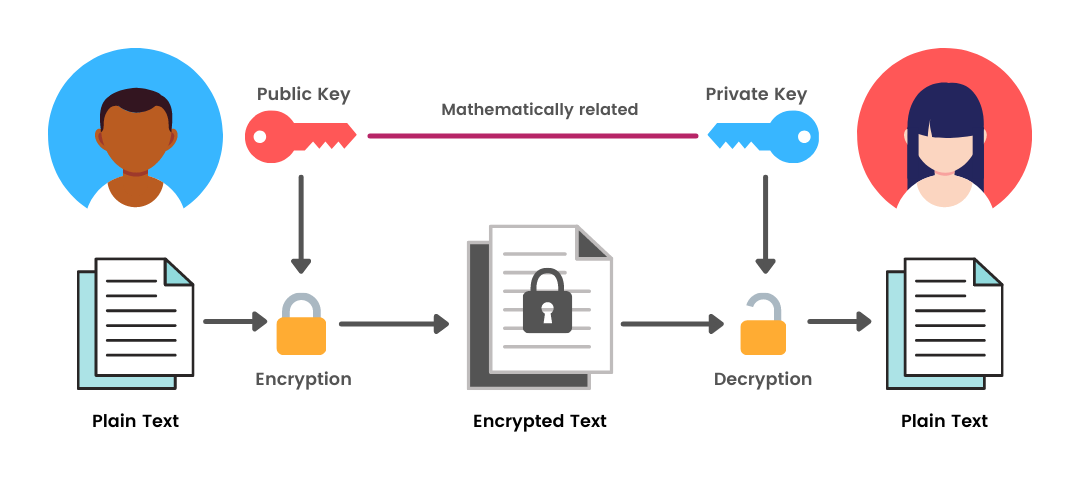
The public key is the one that can be shared with anyone. The private key is secret, and only you know your private key.
You can now ask whether the communication channels are already encrypted, and no one can sniff the data packets. So why the need for E2EE? The answer here is that the data also passes through the multiple intermediary servers where the data is decrypted before and after the transmission, i.e., stored on the server in plain text. Therefore, it can be viewed by anyone who gets a hold of that server’s database. The goal is to make the data accessible only by the sender and the receiver. For example, when you send a text to someone on WhatsApp, the message first goes to the WhatsApp’s server and is redirected to the receiver. If the text is E2E encrypted, even if WhatsApp tries to read the message (or share it with third parties), they can’t convert the ciphertext into readable plaintext.
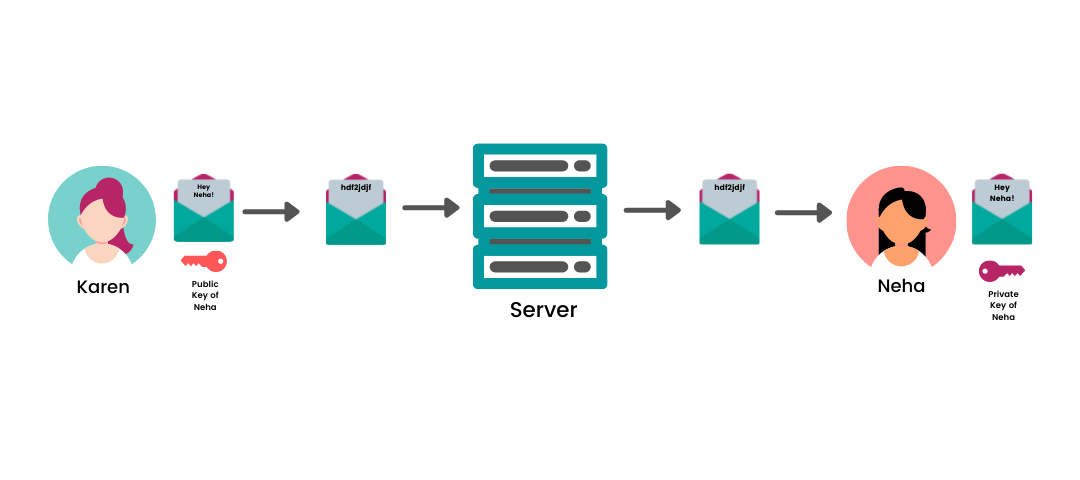
Using E2EE has several other advantages a well:
- Since the data that reaches the server is encrypted, even if there is a data breach and the server is compromised, the attacker would only get obscure data objects that can’t be decrypted. This makes the user's data safe from malicious attackers.
- E2EE prevents potential eavesdroppers as only the individual, which the data is meant for, can decipher it. Not even the service provider itself or a government authority can access the data.
- The E2EE process does not require encryption of routing information, like headers, addresses, and trailers. Instead, the servers on the network read the routing information and pass on the data packets to their path.
- E2EE protects the right to privacy and freedom of speech that every citizen has. But it can’t always be rainbows and unicorns, right?. Just like any form of tech out there, there are situations where this encryption is less desirable. For example, the government in the US has been exploring the idea of banning E2EE as it was harder for them to track people doing criminal activities online .1 Or recently, in India, with the new IT rules, the government wanted to have the ability to trace the origin of contents that pose a potential threat to the country (Fake news, for example). But WhatsApp put down the request citing it could break end-to-end encryption. 2
Just how secure is E2EE?
To say that the encryption is almost unbreakable will not be wrong. But there are challenges that E2EE faces as well. Like the "Man in The Middle Attack" 3 , the attacker impersonates the message’s recipient by substituting his public key with the recipients. So, when the message is encrypted, he has the key that can unlock the cipher. He then encrypts the message with the recipient's public key and sends the message again to avoid detection.
Conclusion
The E2EE, even with disadvantages and challenges, is not going anywhere soon. The reality is that it is protecting our digital privacy, and removing it can have dire consequences. Protecting our personal data from getting into unwanted hands is way more crucial than we realize. Even if people have grudges against this, it goes without saying that until we have a better tool, E2EE is necessary.






















 Batoi Corporate Office
Batoi Corporate Office