
Introduction
As a security officer or IT executive, you might have heard a lot of discussions about maximizing security while reducing user friction. But many times, passwords are susceptible to brute force and phishing. That makes the organization and the individual prone to data breaches, account takeovers, or cyber threats. Also, many of us cannot remember all the different passwords easily. To defeat such hurdles, the passwordless authentication mechanism came into the picture. This article will give you a quick guide on passwordless authentication and how it minimizes risk and enhances user experience and satisfaction.
What is Passwordless Authentication?
We can define passwordless authentication as an authentication technique through which customers and employees can access a system or application without putting in any password or passphrase. It helps verify user identities without using any form of password or memorized secret. Instead of using a password, this authentication method verifies based on the possession factor or inherent factors. These possession factors could be a one-time password, mobile device, proximity badge, hardware token code, magic links, etc. Again, intrinsic elements like fingerprints, behavioral traits, and retina scans are popular. But now the question that pops up is why passwordless authentication and not just simply passwords?
Risks Associated with Passwords
Most of today's work relies on technology and applications. Organizations force their employees to memorize a long and dizzy array of passwords. Organizations also require employees to change passwords frequently. With this overwhelming pressure of remembering and changing passwords, employees and users sprawl and take risky shortcuts by keeping the same password for all applications.
The combination of username and password for authentication is vulnerable. Attackers can analyze and guess passwords, steal credentials through shoulder surfing or phishing techniques, and access the account or sensitive information. Here are some methods that make password-based authentication vulnerable to the organization.
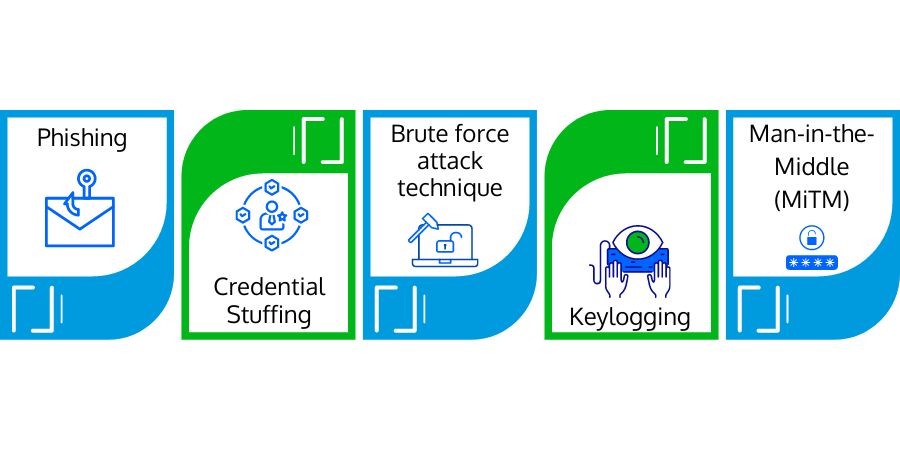
- Phishing: It is a social engineering technique that convinces and tricks the victim into disclosing sensitive information to the attacker or deploying malicious applications on the victim's infrastructure. They send tricky links or phishing pages through bogus emails or text messages.
- Credential Stuffing: It is another form of password threat where attackers try using stolen or leaked credentials of one account to gain access to other accounts. When users try to keep the same password on multiple accounts - this is how their passwords get compromised.
- Brute Force Attack Technique: Through this technique, attackers submit passwords or passphrases (characters, numbers, and symbol combinations) with the hope of guessing and breaking the account password. Cybercriminals use this trial-and-error technique to crack passwords or encrypted keys.
- Keylogging: It is another password attack technique that makes passwords prone to stealing. In this technique, the attacker maliciously puts any keylogger programs (that log keyboard presses). After capturing the username/password keystrokes, these malicious programs send the information to their owner, thus compromising the password.
- Man-in-the-Middle (MiTM): It is another password-compromising technique that intercepts communications streams, and hackers catch the relayed credentials in the middle of the data transmission during authentication. In this technique, the attacker positions himself between a user and an application.
Due to all such problems, passwordless authentication became a boon to the authentication technique.
Reducing Risks through Passwordless Authentication
Passwordless authentication brings robust security by eliminating password compromising and reducing attack vectors. Furthermore, it improves the user experience because it excludes memorizing passwords. Apart from all these, many multi-factor authentication techniques also leverage passwordless authentication to double-check legitimate users. Organizations also deploy passwordless authentication in conjunction with Single Sign-On (SSO) so that employees can utilize the same security token, software tokens, FIDO2-compliant USB keys, mobile apps, or proximity badges for access to all enterprise applications or services.
Benefits of Passwordless Authentication
Passwordless authentication works as a replacement for password-based authentication. It is intrinsically safer and less prone to password threats. Why have enterprises opted for passwordless authentication?
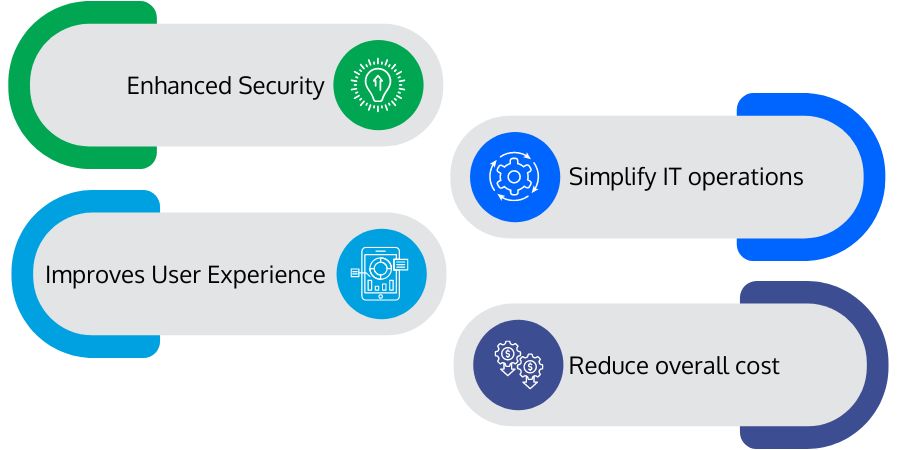
- Enhanced Security: Passwords are the most common attack vector and are accountable for 81 percent of account breaches. Passwordless authentication enhances overall security by eliminating the scope of password-remembering or implementing passwords prone to password-stealing. That eventually reduces credential theft, account takeover, and impersonation.
- Improves User Experience: By minimizing fatigue passwords and blurry passphrases, organizations can enhance user experience. With passwordless authentication, users do not have to remember secret passcodes to streamline their authentication. Users can use biometric signatures, proximity badges, magic links, or physical tokens to gain system access.
- Simplify IT Operations: Passwordless authentication eliminates password compromise issues, rotating passwords, or managing passwords through password managers. It helps IT operations stay safe from attacks like phishing, password spraying, credential stuffing, etc. With passwordless authentication, anyone cannot share their authentication credentials. That delivers complete visibility over identity management and access control.
- Reduce Overall Cost: Managing passwords is expensive. It is because the IT staff constantly monitors & maintains security norms and responds to support tickets. According to Gartner's recent report, the password management cost of an organization lies between $70 and $200 per user per year. The price of a lost password or security breach due to a compromised password is even more. With a passwordless authentication mechanism, organizations can escape such costly situations.
Conclusion
We hope this comprehension has given you a clear idea of what passwordless authentication is and how it is beneficial from passwordless authentication. There is no doubt that passwords are becoming sensitive and the most apparent reason for corporate account takeover (CATO). The best way to avoid password leaks is to either prevent passwords or adopt the passwordless authentication mechanism. Thus leveraging passwordless authentication can eliminate authentication vulnerabilities and reduce password-oriented threats.






















 Batoi Corporate Office
Batoi Corporate Office